The OWASP Top 10 is a globally recognized framework that traditionally identifies the ten most critical security risks in the web and application space within the IT world. It has now expanded into operational technology (OT) environments. The newly created OWASP OT Top 10 includes inadequate authentication, insecure remote access, and insufficient monitoring among other things. These threats have the potential to disrupt operations and compromise safety.
The purpose of this project is to raise awareness, provide practical guidance, and assist individuals within organizations in prioritizing their cybersecurity efforts. By distilling complex risks into actionable insights, the OWASP Top 10 for OT helps engineers strengthen their defenses and enhance resilience against evolving threats.
Why a Top 10 for OT Security?
Categorizing the ten most likely and most severe threat categories seen across different industries can help prioritize and provide guidance on how to deal with the threats. There are also related standards for each category that allow risks to be assigned to specific parts of the standard. These standards include industry best practices, such as ISO2700 and IEC62443, as well as legislation, such as the NIS Directive, and established community-driven frameworks like the MITRE ATT&CK Matrix.
According to ot.owasp.org, this project's main purpose is “to raise awareness about the top security risks and vulnerabilities specific to operational technology (OT) environments. By providing actionable recommendations, we aim to improve the security posture of OT systems and protect critical infrastructure from cyber threats.”
Among other uses, it can serve as a guide for smaller utilities on where to begin their security efforts and as a reference source for utilities already well into securing their substations and grid.
Another main purpose is to help IT experts better understand OT pain points better and to translate between the IT and OT worlds.
Applying the OT Top 10 in Reality
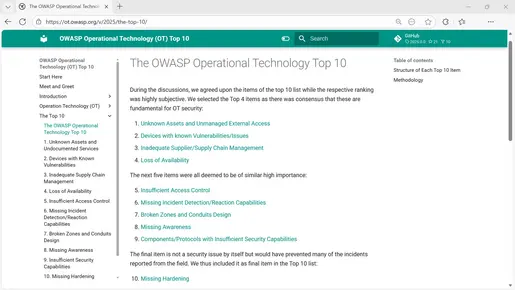
Regarding the first item on the list, “Unknown Assets and Undocumented Services,” it can be said that this occurs in every environment. In an IT context, this could refer to database servers, mobile phones, or notebooks. In the OT world, we mostly refer to IEDs and other dedicated OT devices when we talk about assets. Are surveillance cameras, therefore, assets? YES! However, not only the “assets” described earlier can be problematic if they are not documented and managed. External access is a “necessary evil” in all OT and IT environments. The OT Top 10 list describes the risks associated with this topic, provides well-known examples of real-world attacks, and offers mitigation strategies and countermeasures. You can also find references to standards, frameworks, legislations, and appropriate investigative tools at the end of each item.
However, given with the nature of such top10 lists, there is much more out there than is listed:
The OWASP OT Top 10 should be your starting point, helping you to identify some of the most critical risks associated with OT technology. As you progress on your security journey, you will identify many more. Once you have dealt with the applicable Top 10 items within your environment, you will have the tools and knowledge of how to tackle every subsequent risk.
Learn more about the OWASP Top 10 for OT at https://ot.owasp.org and join us in making operational technology safer for everyone.
Community Effort for OT Cybersecurity | OWASP & OMICRON
The Open Web Application Security Project (OWASP) Foundation has long been a staple in providing standards and guidelines for the community. Initially, it only focused on web technologies and core IT functions. To benefit the wider IT community, they branched out into other fields.
At OMICRON, however, our primary focus is on the energy sector. Nevertheless, we recognize the importance of cybersecurity in operational technology (OT) environments. As industries increasingly rely on interconnected systems, the risk to critical infrastructure grows exponentially. Legislators have acknowledged this need, making security measures mandatory in our industrial environments. To address these challenges, the OWASP Top 10 for OT was created with the support of OMICRON employees and resources.
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?