OT/ICS
Vulnerability
Management
Identify security risks and protect your facility from threats!
Your operational technology (OT) will thank you: A proper OT vulnerability management reveals vulnerabilities in your OT assets and OT environments as whole, so you can implement protective measures, such as continuous IDS monitoring. This allows you to respond immediately to unauthorized activity and quickly restore normalcy through targeted remediation.
The more detailed the information about your assets, the easier it is to detect and prioritize events and alarms.
Enhancing Cybersecurity of
Critical Infrastructure
Outdated software of protection and control devices seem often impossible to update. Security patches require costly maintenance and disrupt critical processes. The risk of attacks and ransomware continues to grow.
The problem with security advisories
Why information management is so valuable
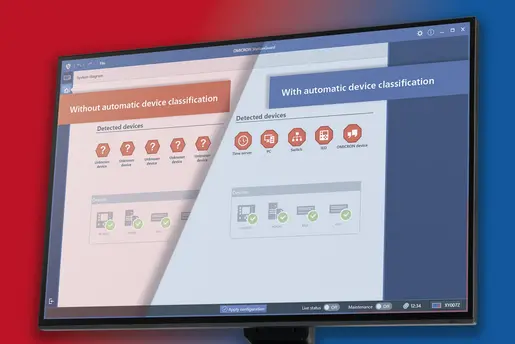
Why do you need a comprehensive
asset inventory?
Do You
Know Your
Vulnerabilities?
We can assess your security risks. You will gain:
- Insight into all cybersecurity and functional aspects
- Identification of attack surfaces and vulnerabilities
- Detection of functional problems in the network and automation system
- Asset inventory for full visibility of OT components
Holistic Safety Assessment
for Your OT Utility
Security risk
assessment with dashboard
Functional
monitoring for everyone
Vulnerability
detection of your OT network
Detailed asset scanning
Continuous OT Vulnerability Management
Gain visibility into vulnerabilities across OT assets, devices, and software – with security insights tailored to industrial environments.
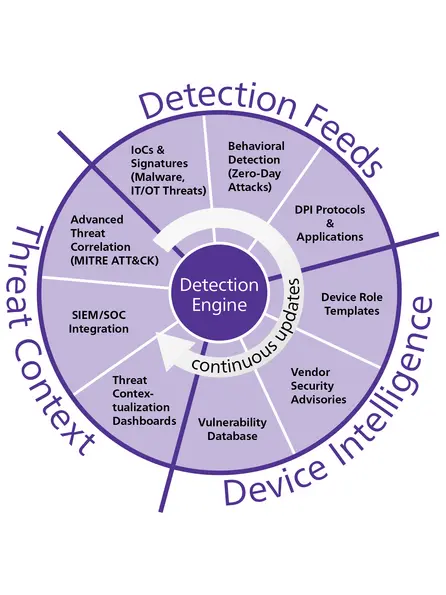
OMICRON Threat Intelligence
Stay Informed & Make the
Right Decision
OMICRON’s Threat Intelligence (OTI) delivers updates to protect IT and OT networks from evolving cyber threats. These include:
✔️ Updated detection rules (IOCs), including Suricata signatures for malicious network traffic
✔️ Enhanced anomaly detection
✔️ Deep Packet Inspection (DPI)
✔️ Device role template updates
✔️ Advanced threat correlation
✔️ SIEM/SOC integrations
✔️ Threat contextualization for dashboards
✔️ An up-to-date OT vulnerability database
OTI is focused on detection engineering to always keep your assets safe and you informed.
User Interface for Powerful
Vulnerability Management
Detect weak points immediately
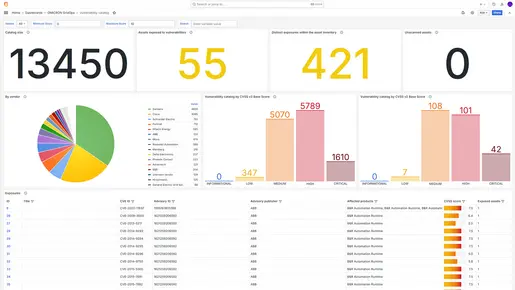
Our vulnerability dashboard lets you instantly identify vulnerabilities and their threat level. It provides continuous information about potential threats.
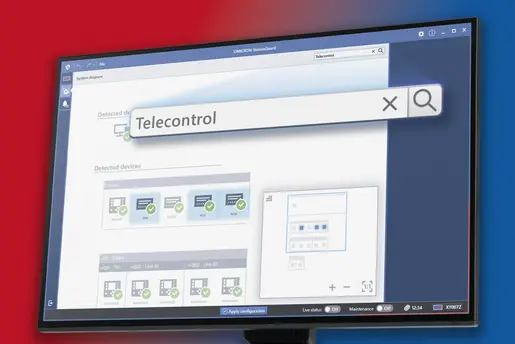
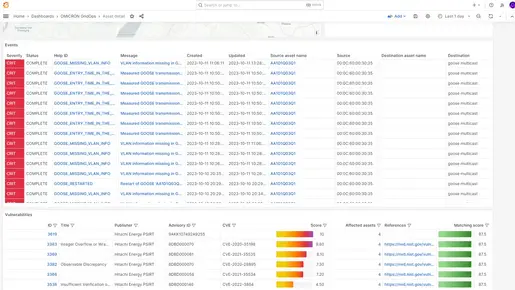
Intelligent scanning for OT vulnerabilities
CVE (Common Vulnerability Exposure) analysis made easy: Use our vulnerability database to quickly determine which systems a specific CVE affects and which security advisories are relevant to you.
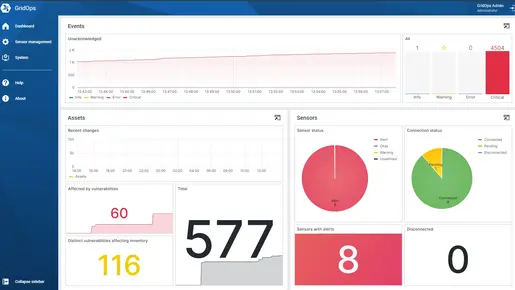
Visibility for all stakeholders
Generate overviews for reports with relevant information for management, suppliers, and auditors to prioritize risks. Visualize the cyber risk to your energy network with our help. Our visibility improves your understanding of your security posture.
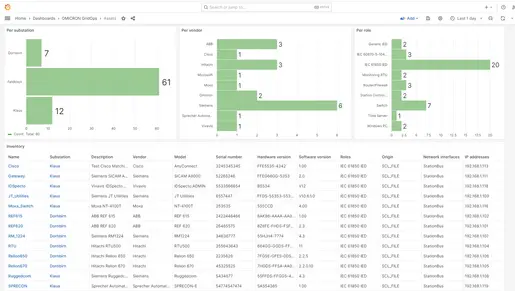
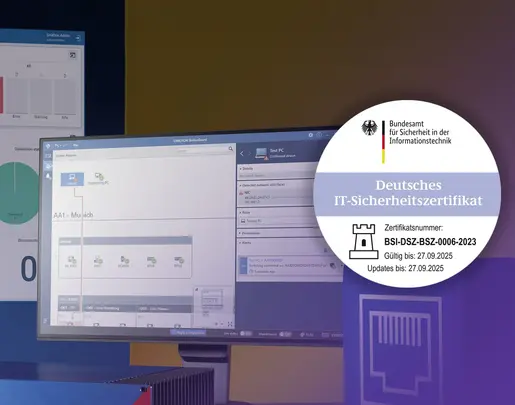
Supported by a precise equipment inventory
Our StationGuard solution compiles an asset inventory with detailed information from multiple sources to provide the best possible foundation for vulnerability management.
Resources
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?