The National Institute of Standards and Technology (NIST) has released version 2.0 of its Cybersecurity Framework (CSF), updating it for the first time since 2014. The new version broadens its scope to help all organizations, not just critical infrastructure, manage cybersecurity risks.
The aim of the Framework is to share best practices on how to understand, assess, prioritize and communicate cybersecurity risks.
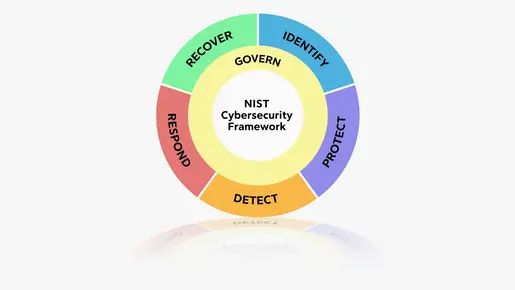
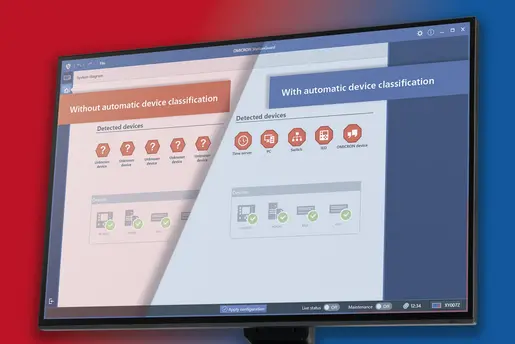
The NIST Cybersecurity Framework Version 2.0 brings some important changes for security managers. The new "Govern" feature emphasizes the importance of cybersecurity in governance and risk management. This is also a topic that is becoming more relevant with the NIS2 implementation. Expanded guidelines and specific implementation examples make it easier for practitioners to apply in the OT sector. Additional resources support supply chain security and global applicability ensures that international standards are considered. These updates significantly improve the protection and management of OT infrastructures.
The detection function has been restructured and expanded. The requirements have now become much more comprehensive. This underlines the increasing importance of anomaly detection for the security of companies.
The New NIST Features at a Glance
How Is the NIST Cybersecurity Framework (CSF) 2.0 Structured?
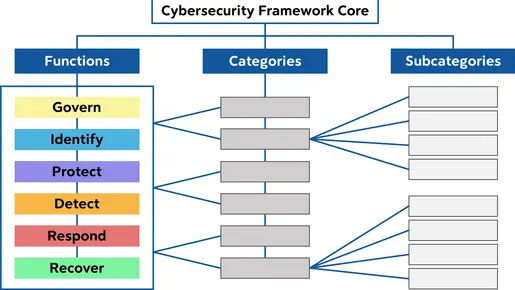
The framework is split into three sectors: The CSF Core, the CSF Organizational Profiles and the CSF Tiers. The aim of this framework is to understand, assess, prioritize and communicate cybersecurity risks in a controlled and standardized way.
According to the framework, all voluntary actions that support functions GOVERN, IDENTIFY, PROTECT and DETECT should all happen continuously.
However, actions that support RESPOND and RECOVER should be ready at all times and we operational when cybersecurity incidents occur.
What Are the CSF Profiles?
The CSF Organizational Profile defines an organization's current or desired cybersecurity status based on the Core's outcome. It guides actions by considering the organization's mission, stakeholder expectations, threats, and requirements. Every Organizational Profile includes one or both of the following:
Current Profile
Target Profile
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?