Essential OT Security Functions
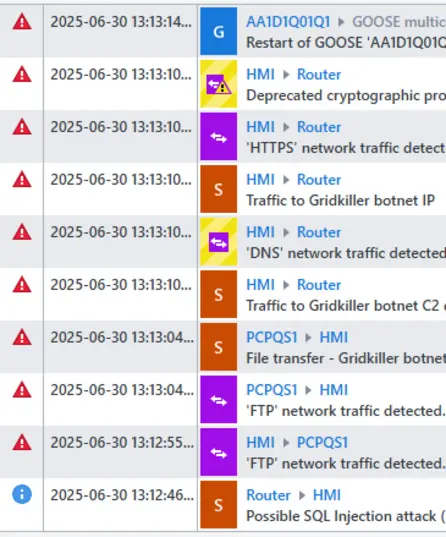
Intrusion Detection
Know What’s Normal, See What’s Dangerous
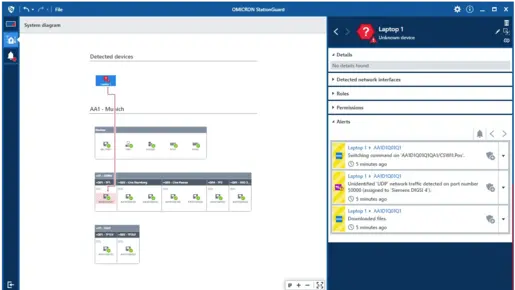
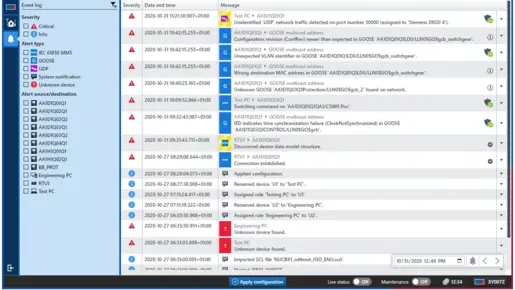
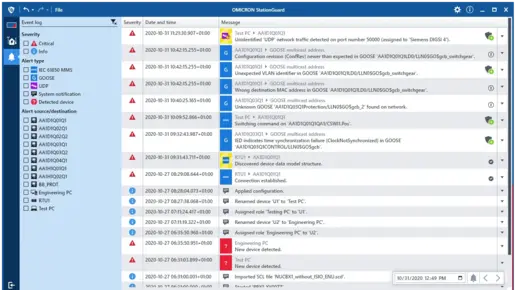
StationGuard monitors your communication networks in real time, reliably detecting cyberattacks, unauthorized activities, and misconfigurations.
The solution combines deep protocol understanding with security-focused expertise:
✔️ Intrusion detection based on defined behavior patterns
✔️ Signature detection of threats and indicators of compromises (IOCs)
✔️ In-depth analysis of OT-specific communication protocols
✔️ Clear, actionable alerts with technical and security context
This gives you full awareness of what’s happening in your network – and whether it poses a risk. You stay in control: for stronger security, fewer false alarms, and faster response in critical situations.
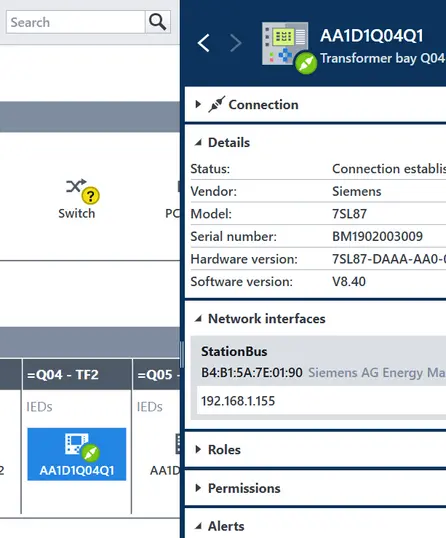
Asset Identification
Discover, Understand, and Protect Your Assets
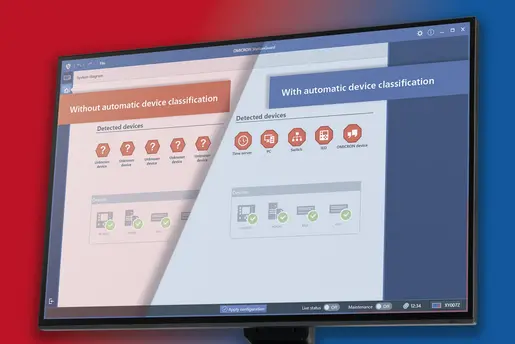
StationGuard precisely and continuously identifies all assets in your network – without active scanning or additional sensors.
The solution uses deep protocol analysis and domain-specific knowledge from protection and control systems:
✔️ Automatic detection and classification of IEDs, RTUs, gateways, SCADA systems, and more
✔️ Extraction of key device data such as type, firmware version, and serial number
✔️ Reliable identification even with sporadic communication or passive assets
The result: a complete, up-to-date view of your OT landscape – essential for security analysis, troubleshooting, and audits.
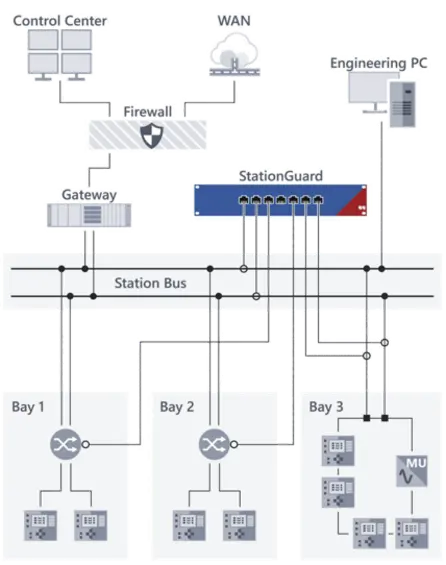
Functional Monitoring
Security Through Seamless
Functional Control
StationGuard continuously monitors the functional health of your OT systems, detecting deviations, faults, and potential disruptions early. This way, you keep full control over your operations:
✔️ Comprehensive monitoring of critical processes and communication paths
✔️ Early warning system for malfunctions and anomalies
✔️ Detailed analysis for fast root cause identification
With StationGuard, you always know your systems are running reliably. This builds confidence, reduces downtime, and enables swift response when it matters most.
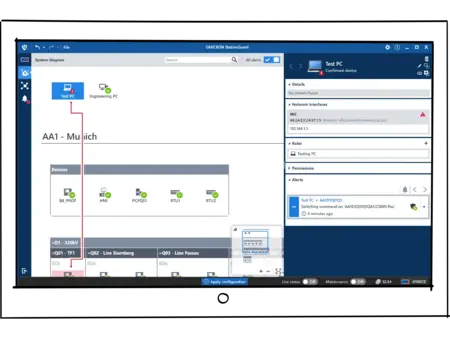
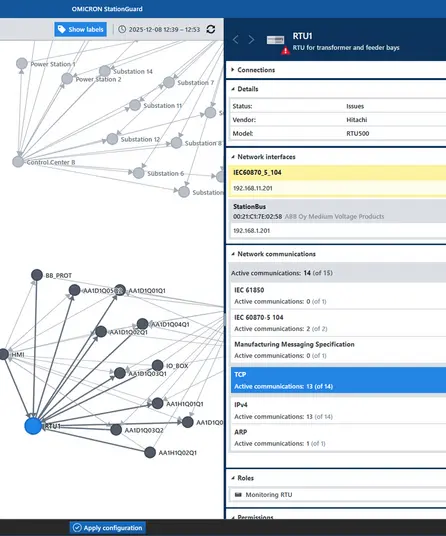
Live Network View
Complete Visibility
into Your OT Network
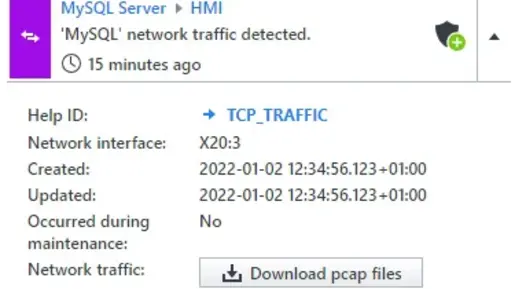
Real-Time Network Communication Monitoring
The Overview of Network Communication feature provides comprehensive insights into your OT network. It shows you exactly what is happening in your network:
✔️ Who communicates with whom
✔️ Which protocols are being used
✔️ How data flows – live and historically
Your key benefits
✔️ Interactive visualizations for better understanding
✔️ Real-time insights into active services
✔️ Anomaly detection for faster response times
✔️ Contextual analysis of communication paths
Easily transform complex raw data into clear, actionable intelligence for enhanced security and performance of your industrial systems.
Lessons
learned from
100 +IDS
Deployments
Read our article and learn how security and operational risks in OT networks can be systematically identified:
- Detection of security vulnerabilities and operational anomalies
- Analysis of real network communication in substations, power plants, and control centers
- Assessment of the most common and critical risks
- Derivation of robust, cyber-resilient OT network architectures
The analysis not only reveals security problems, but also previously hidden deficiencies in the station and process bus.
Read the Article HereDownloadable Documents
We are ready to guide you
Take a decisive step towards a comprehensively secure OT network
- Do you have a question?
- Need more information?
- Would you like to request a demo?
Request a demo!
Ready to experience the power of StationGuard?
Schedule a demo today and witness firsthand how our innovative cybersecurity solution can fortify your critical infrastructure against potential threats and vulnerabilities.
Schedule an AppointmentImmediate Protection
& Other Benefits of Our Solution
Downloadable Documents
We are ready to guide you
Take a decisive step towards a comprehensively secure OT network
- Do you have a question?
- Need more information?
- Would you like to request a demo?
Request a demo!
Ready to experience the power of StationGuard?
Schedule a demo today and witness firsthand how our innovative cybersecurity solution can fortify your critical infrastructure against potential threats and vulnerabilities.
Schedule an AppointmentStationGuard GridOps -
Central Management System
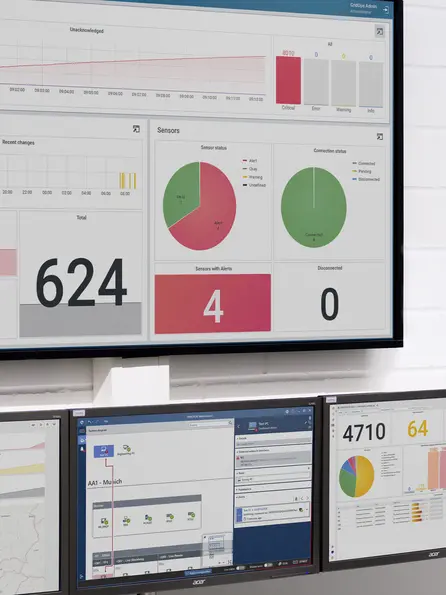
GridOps is the management component of the StationGuard Solution. It enables you to manage all your cyber risks in one place. It integrates threat and alert analysis into a clean, flexible user interface. It provides detailed reporting, complete visibility, and collaboration interfaces. Combined with the most accurate asset inventory, GridOps shows you only the vulnerabilities that matter to you.
You benefit from:
✔️ Unified interface for seamless access to alert trends and statistics, global asset inventory, and network visibility.
✔️ Visualized asset inventory and associated security risks, threats, and malfunctions, so you can track overall security posture.
✔️ Sped-up analysis and investigation with automated data enrichment and context.
✔️ Centralized communication to keep your IT and OT teams in the loop.
✔️ Improved decision-making processes and efficiency within the organization.
Its vulnerability management features can be acquired individually or in combination with the StationGuard Sensors.
Downloadable Documents
We are ready to guide you
Take a decisive step towards a comprehensively secure OT network
- Do you have a question?
- Need more information?
- Would you like to request a demo?
Request a demo!
Ready to experience the power of StationGuard?
Schedule a demo today and witness firsthand how our innovative cybersecurity solution can fortify your critical infrastructure against potential threats and vulnerabilities.
Schedule an AppointmentFind the Right Platform
for Your Network
Our platforms provide powerful and secure solutions for cyber security and digital asset surveillance. Compare our platforms RBX, MBX, and VBX and discover which one is the right fit for you!
RBX Permanently installed 19" platform

- Guaranteed to be cyber secure with crypto processor, secure boot and hard disk encryption.
- Multiple Ethernet interfaces for separate networks with timestamp support.
- Powerful and robust: 4 cores, 450 GB memory, 16 GB RAM.
- Temperature resistant, tested 19" platform with no moving parts.
- Secure I/O, hardware failures are reported immediately (via watchdog contact).
MBX Mobile and DIN rail mountable platform

- Powerful quad-core processor for complex plant applications and system visualization.
- 4 SFP slots for secure fiber and Ethernet connections to SAS network segments.
- PC isolation, easy IP address configuration for IED simulation.
- Crypto processor and hard drive encryption for maximum system security during testing.
- Availability of permanent installation on a DIN rail.
VBX Virtualized platform

- Virtualized platform for the StationGuard sensor.
- Deployment on existing substation and control center computing platforms.
- Rapid installation and maintenance.
- Easy backup and recovery.
We are ready to guide you
Take a decisive step towards a comprehensively secure OT network
- Do you have a question?
- Need more information?
- Would you like to request a demo?
Request a demo!
Ready to experience the power of StationGuard?
Schedule a demo today and witness firsthand how our innovative cybersecurity solution can fortify your critical infrastructure against potential threats and vulnerabilities.
Schedule an AppointmentAbout StationGuard- and
GridOps-Features
How does OMICRON ensure that the StationGuard IDS does not impact the availability of my assets?
StationGuard is a passive IDS that does not interact with your equipment. The connection via mirror ports (also known as SPAN ports) ensures that the IDS cannot send any packets into the network.
Does the StationGuard solution provide real-time alerts and notifications? Can it automatically respond to detected threats?
All events and alerts detected by StationGuard are immediately reported in the StationGuard and GridOps user interfaces, logged on the sensors along with forensic evidence, and routed. In addition, your staff can be separately notified of events and alerts via email according to your reporting and escalation paths.
Because StationGuard is a passive IDS, it does not actively interfere with network traffic or execute commands/switches. In addition, it is possible to implement automated processes that execute pre-programmed automatic responses (e.g., via a SIEM system). This would allow a SIEM or SOAR system to automatically activate firewall rules to block the IP addresses in question after a StationGuard alert, for example.
Can I integrate the StationGuard IDS with my ActiveDirectory or LDAP system?
Yes, LDAP/Active Directory integration can be managed and configured through the GridOps central management system.
How are users and permissions managed? Can I manage roles and permissions myself?
To ensure secure access to your StationGuard instances, you can define different roles and access rights via our central management system GridOps. For example, you can specify that only authorized personnel can make configuration changes or enter maintenance mode. With Role-Based Access Control (RBAC), threats can be reduced and even eliminated.
How exactly does vulnerability management or the vulnerability database help me?
GridOps has a vulnerability database that monitors all your assets or resources live for vulnerabilities. This database contains all security advisories published by device vendors for each asset. GridOps has a built-in device database that can identify sub-components, plug-in cards, and their firmware versions to provide the most accurate vulnerability management for protection and control devices.
With our built-in vulnerability management, GridOps shows you
- which of your protection and automation devices are affected by a disclosed vulnerability (CVE or Security Advisory),
- automatically assesses their criticality based on CVSS, and
- shows you remediation options, such as a firmware update or configuration advisories.
What is DPI and which protocols are supported?
For IT and OT protocols, our attack detection system includes advanced and effective anomaly detection based on our integrated Deep Packet Inspection (DPI) to protect against cyber-attacks at an early stage. We perform a detailed analysis of transmitted data packets and their content on the network.
StationGuard supports over 30 OT protocols, such as IEC 61850 MMS, GOOSE, IEC 62439-3 PRP and HSR (with RedBox), IEC 60870-5-104, DNP3, Modbus TCP, IEC 62056 (DLMS/COSEM), IEEE C37.118 (Synchrophasor), IEEE 1703-2012 / ANSI C12.22 (AMI Protocol), IEC 60870-6 (ICCP/TASE.2 - UCA 2.0), SIEMENS S7, EtherCAT, and Profinet.
StationGuard supports over 300 IT protocols, such as FTP, HTTP, HTTPS (without decryption, but with application detection), RDP, NTP, NetBIOS (Windows File Sharing), ARP, DHCP, MySQL, MSSQL, PostgreSQL, SSH (without decryption, but with application detection), Telnet, ICMP / ICMPv6, RIPv2, SSDP, and MDNS.
What is Functional Monitoring?
An additional feature of our StationGuard intrusion detection system is the integrated functional monitoring of the plant network. This allows you to monitor not only cybersecurity parameters, but also the proper operation of your automation systems and networks to detect deviations from the target state of the plant. This can include interoperability problems between devices, configuration errors, exceeded transmission times and failed time synchronization.
How does StationGuard detect intrusions?
The key difference between StationGuard and other OT IDSs is the methodology used to establish the baseline. StationGuard employs a whitelist mechanism, which could also be regarded as a baseline. However, the crux of the matter is the manner in which the baseline is established.
Other IDSs use a baseline derived from the traffic observed during the initial two-week period. It is not feasible to anticipate every eventuality in the lifecycle of a substation within this period. This could result in an unacceptably high number of false positives for these learning-based systems.
StationGuard leverages the system's specifications by importing project files, such as 61850 SCL format. By importing these project files and specifying the device roles, StationGuard is able to ascertain the purpose of each device and the function and traffic that will occur. This allows it to establish a more tailored baseline, resulting in a significantly lower number of false alarms than comparable solutions.
All substation IEDs are serviced once every three to five years. How do you prevent false positives during maintenance?
It is likely that a significant number of cyber security alerts will be generated by the intrusion detection system when maintenance is conducted at substations. It should be noted that general maintenance is not typically conducted at three-to-five-year intervals, as there are numerous instances where maintenance is required with greater urgency.
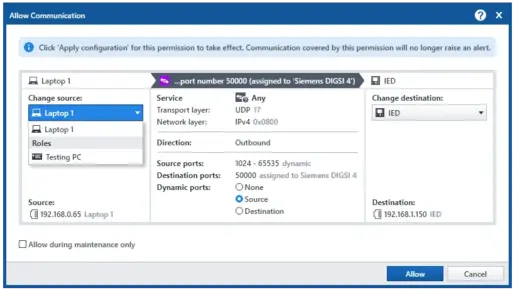
To prevent unnecessary alarms, StationGuard has a maintenance mode that allows users to notify the IDS that maintenance is occurring at the substation. This enables maintenance teams to perform additional tasks, such as accessing web interfaces or using engineering protocols, without triggering an alarm. During normal operation, these activities are not permitted. This approach ensures high detection accuracy during normal operation while limiting false alarms during maintenance.
Is StationGuard connected to a threat intelligence source?
Yes. The nature of threat intelligence in this domain of operational technology differs from that of information technology. It is worth noting that there are only a limited number of exploits that are exclusive to these OT devices and their respective vulnerabilities.
However, there is a significant body of knowledge surrounding the vulnerabilities themselves. We provide a vulnerability database that has been tailored specifically for these devices. We have implemented device type matching for all OT devices in the power grid, enabling us to provide the vulnerabilities that you need to look out for.
Subsequently, the threat intelligence source is updated via our detection engine. Our detection engine offers a comprehensive range of detection capabilities, and we provide continuous threat intelligence updates in the form of detection engine updates to all of our StationGuard sensors.
Is it possible for attacks to come from GOOSE messages? If so, how do you deal with them?
For GOOSE, the IEC 62351 standard enables GOOSE security, with the primary objective being to add authentication to GOOSE messages, identify the sender, and prevent any tampering.
However, the IEC 62351 standard has yet to be widely adopted in substations. There are only a handful of utilities utilizing this technology, and it is only in pilot projects at this stage. The technology is not yet sufficiently developed for widespread use.
To address these challenges, StationGuard has implemented over 35 comprehensive checks for the GOOSE protocol. This is due to the fact that there is a vast range of potential attacks, given that GOOSE is based on multicast, and essentially anyone can send a GOOSE message that fits the criteria. Furthermore, there are numerous ways to spoof GOOSE messages and disrupt GOOSE communication, many of which are sophisticated and difficult to detect. StationGuard is designed to identify and neutralize these threats.
Substations have both critical and non-critical substation automation systems. How does your solution separate and protect these systems based on their criticality?
In SAS communications, all devices use OT protocols, and we categorize them based on their role and the function of the device. StationGuard can discern their behavior and monitor their activities closely. Our IDS is able to accurately identify the activity associated with these protocols.
As a result, it determines which individuals are authorized to control a breaker and which other devices are only allowed to send simple setting commands, for example. While both devices are sending commands over OT protocols, the nature of the control they exert is entirely distinct. StationGuard is designed to discern this difference.
Furthermore, other devices such as IP cameras and CCTV also have designated roles and are only permitted to communicate via specific protocols. They are not allowed to use any critical OT controllable protocols. This approach enables the effective segregation of devices based on their functionality and criticality.
Additionally, for RTUs, it is possible to differentiate between read-only RTUs and controlling RTUs, thus facilitating the differentiation of criticality levels here as well.
How does StationGuard manage device updates and replacements within substations?
Given that StationGuard's approach to anomaly handling is based on establishing a baseline of allowed devices and communications, it is important to note that simply plugging in your equipment may trigger unknown device alarms. This is due to the fact that the system is designed to identify and flag any new devices that may not have been previously identified.
However, you can simply accept the device and assign it a role. You can even reuse the roles you have for the previous device, and it will work seamlessly. You can then delete the old device if you have removed it from the system.
Alternatively, you always have the option to upload the new version of the 61850 SCD file for the project and then automatically update all the devices based on it.
Which IEC 61850 protocols are supported by StationGuard?
All of the IEC 61850 protocols. We support deep packet inspection for MMS and GOOSE as well as for Sampled Values. StationGuard also supports the redundancy protocols HSR and PRP, which are related to but not part of the 61850 standard.
Additionally, our solution integrates time synchronization protocols, including PTP and NTP, which are related to 61850 but not directly included in the standard series.
Also the SCADA communication protocols, IEC 60870-5-104 and DNP3, are implemented with the necessary depth. In the case of 104, for instance, we differentiate according to the criticality of the task at hand, whether it concerns the control of a breaker or not.
How can StationGuard be patched if it is running locally with no remote access?
An update of StationGuard can be initiated as soon as a connection (remote or local) is established.
How do you patch legacy systems that have high vulnerability ratings?
It is essential to conduct a comprehensive risk assessment before implementing patches in any operational technology (OT) system. It should be noted that patching is not always the optimal solution. In many cases, alternative mitigation strategies can effectively serve as a substitute for direct patching.
If patching is deemed necessary, it is advisable to first apply these patches to identical assets in a controlled laboratory environment to ensure that the integrity of their configuration remains intact. It is then essential to temporarily suspend operations within the OT network to prevent any unforeseen disruptions that may occur during the patching process.
This suspension can be either a pre-planned operational downtime or performed during an unforeseen business interruption. The opportunity to temporarily suspend operations allows for extensive testing of the configuration of your assets to confirm their operational safety. A practical example of such a suspension could be the de-energizing of an electrical substation to ensure a safe environment for patch implementation.
What are the benefits of using StationGuard in an SDN network?
Networks using Software Defined Networking (SDN) have an inherent "deny by default" policy. To test this characteristic, we have conducted research on SDN switches from SEL. The findings revealed numerous benefits of using SDN in conjunction with StationGuard.
SDN switches have dedicated mirror ports that StationGuard can use to verify the security of the traffic being allowed through the SDN switch. This includes checking the integrity of the protocols and detecting any spoofed connections. The configuration of the SDN can also be verified by StationGuard, as any allowed traffic that should not be permitted will be detected by StationGuard. Configuration verification can also be done vice versa.
What is the process for updating allow list (whitelist) rules to reflect changing protocols?
We provide software releases to our customers on a biannual basis. In addition, we offer a range of testing solutions for use in operational technology (OT) networks that adhere to OT protocols. This division of our business provides us with a comprehensive understanding of the patterns used in OT protocols, which enables us to develop the necessary allow list rules.
Does StationGuard include identity and access management?
StationGuard supports Active directory and RBAC.
Is a SIEM builit into StationGuard? If so, how does it retrieve security logs to implement WORM?
StationGuard is not a SIEM solution. StationGuard provides its logs to the SIEM solution via syslog.
Can StationGuard process serial protocols (60870-5-103)?
Yes, if StationGuard is mapped to TCP/IP.
Will StationGuard support IoT devices?
StationGuard will detect traffic from IoT devices in monitored zones.
Can StationGuard analyze proprietary protocols?
StationGuard classifies each protocol and verifies its integrity to ensure it conforms to expected standards and behavior.
About the Integration of
OMICRON's Solution
Does StationGuard require a setup period/learning period?
OMICRON has developed a novel Allowlist approach based on its many years of expertise in the field of power analysis. In contrast to conventional signature- or learning-based IDS approaches, this approach enables our StationGuard IDS to be used immediately without a learning period and with improved detection of security-relevant events and faults. The typical commissioning time for StationGuard is 1-3 hours per plant network. After this time, StationGuard is fully parameterized and ready for use without any additional training time.
How easy is it to configure and manage the StationGuard solution? How much IT expertise is required?
StationGuard has been designed from the ground up to allow plant operators to operate and configure the intrusion detection system. The training required can be estimated to be as little as one day. StationGuard's built-in knowledge of the system gives it the advantage of requiring little system or IT knowledge from the operators themselves. However, our experts are always available on site or by phone for planning and configuration.
How does OMICRON support me with the integration, installation, and configuration of the IDS?
To ensure a smooth and optimal start of the StationGuard IDS, we support you with our best practice approach. To this end, we first discuss your deployment and application requirements, as well as the structural design of your operator's plant. Our staff will then perform the user-specific pre-configuration of your StationGuard. Installation and integration are carried out by our expert staff at your site.
If desired, we can work with your staff to perform a security assessment of your OT networks and systems.
How does an IDS solution integrate with other security tools and systems in my organization's security infrastructure?
StationGuard and GridOps can easily connect to SIEM and ticketing systems (such as Splunk, FortiSIEM or ServiceNow) via built-in plug-ins. Our easy-to-understand alerts can also be forwarded via the Syslog protocol.
Asset data, e.g., from OMICRON ADMO or ERP systems, can be imported into StationGuard to complete the asset information. By exporting the asset or working capital list from StationGuard to ticket systems, you can easily update, reconcile, and document your asset inventory.
Integration with ticketing systems allows you to automatically create tickets to handle IDS alerts. Tickets can also be automatically assigned to the employee(s) responsible for the asset or location through an imported asset directory.
How can I protect myself from attacks during commissioning, testing, and maintenance?
To protect against cyber-attacks during testing or maintenance of your equipment, we support you with a specially developed "maintenance mode". This can be quickly and easily enabled or disabled via StationGuard. To ensure that no false alarms are triggered even when authorized tasks are being performed, the engineering PCs and test equipment used can be registered in advance in StationGuard. This method can also be used to monitor the activities of service providers during commissioning. This flexible approach allows StationGuard to monitor assets prior to factory acceptance.
We are happy to help you
Take a decisive step towards a comprehensively secure OT network
- Do you have a question?
- Need more information?
- Would you like to request a demo?
Request a demo!
Ready to experience the power of StationGuard?
Schedule a demo today and witness firsthand how our innovative cybersecurity solution can fortify your critical infrastructure against potential threats and vulnerabilities.
Schedule an Appointment