Intrusion
Detection
for the
Power Grid
Comply with legal requirements and detect cyber attacks immediately!
Protecting power generation, transmission, and distribution networks from cyber attacks is critical for maintaining the supply’s security. Cybersecurity intrusion detection systems continuously monitor network traffic and behavior, promptly identifying and alerting to potential cyber threats and vulnerabilities - giving you the chance to react in time!
Overcome Typical IDS Challenges with StationGuard
Reliable alerts save costs & keep your team focused
Cost-efficient IDS setup with
minimal effort
Smooth interaction between IT (SOC) & OT
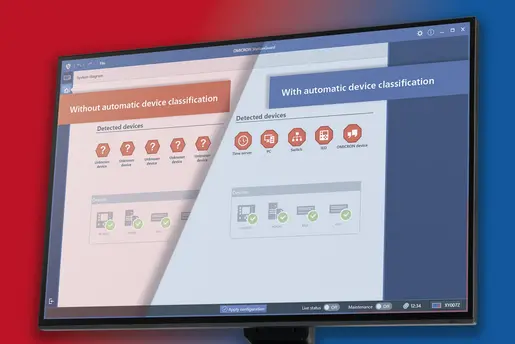
Easily keep track of OT assets across all plants
Full Network Understanding
with Clear Visualization
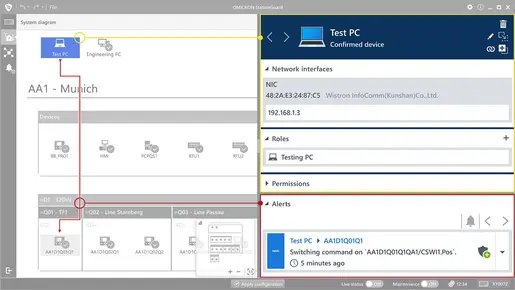
Contextualize Alerts in ZeroLine Diagram
SOC Analysts can rely on built-in OT knowledge. The resulting contextualization of the alerts speeds up incident response.
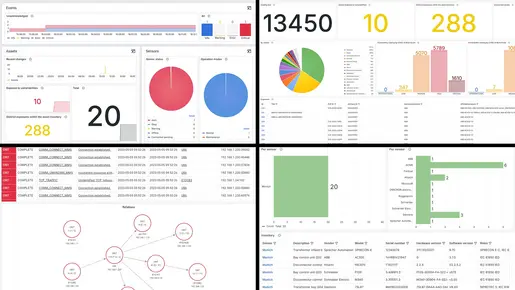
From the Grid Level …
Multiple dashboards offer a comprehensive overview of all network statuses.
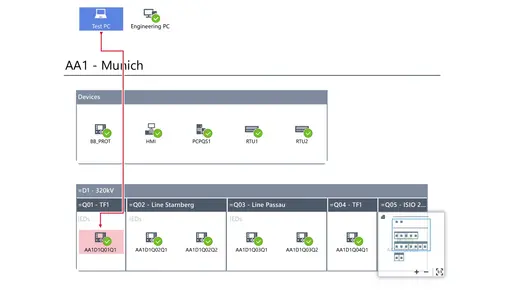
… to the Plant Level …
An intuitive network visualization allows immediate detection of events.
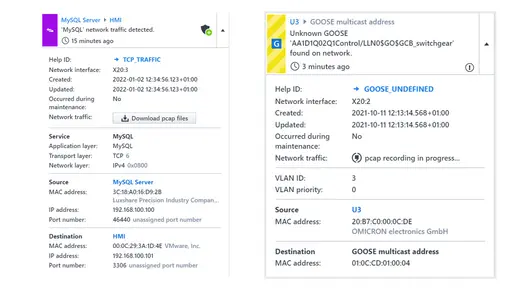
… Down to the Device Communication
With the option to visualize every asset and its communication individually.
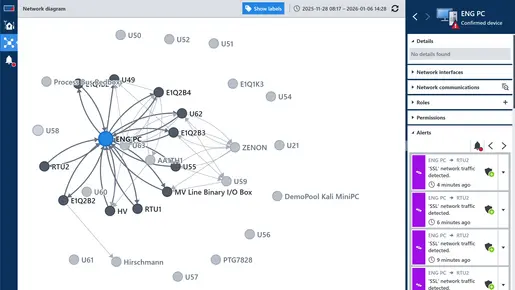
Powerful Network View
See details on devices, protocols, and communication flow to spot suspicious activity at a glance.
StationGuard's
Intrusion Detection Techniques
Signature
Detection
Behavioral
Detection
Allow Listing
Functional
Monitoring
Documents
Resources
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?