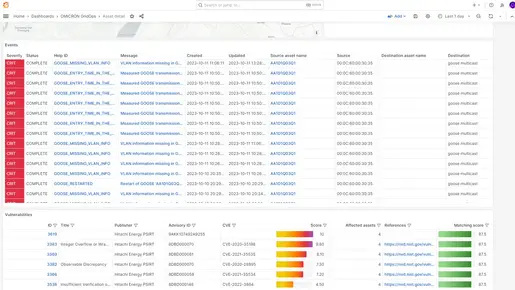
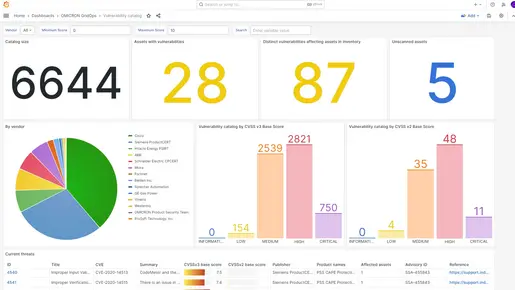
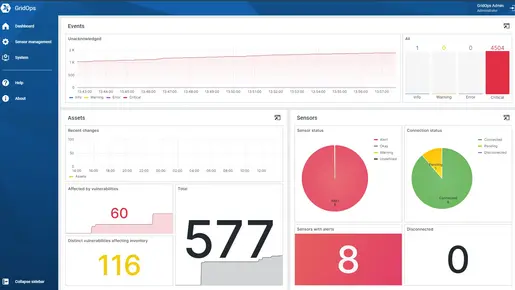
Reveal vulnerabilities in your system and implement protective measures, such as continuous IDS monitoring. This allows you to respond immediately to unauthorized activity and quickly restore normalcy.
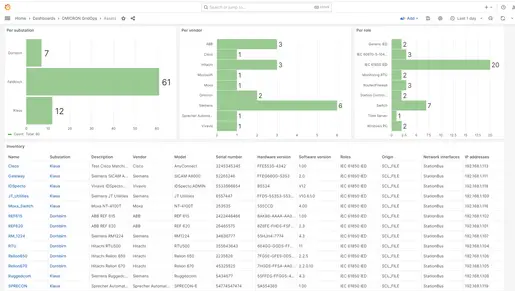
The more detailed the information about your assets, the easier it is to detect and prioritize events and alarms.
Comprehensive Vulnerability
Management
- Holistic approach to security risk assessment
- Insight into all cyber security and functional aspects
- Identification of attack surfaces and vulnerabilities
- Detection of functional problems in the network and automation system
- Asset inventory for full visibility of OT components
Contact Us!
We’re looking forward to helping you.
- Have a question?
- Need more information?
- Would you like to request a demo?